Routeros Change Software Id
Let's Encrypt certificates for RouterOS / Mikrotik
UPD 2018-05-27: Works with wildcard Let's Encrypt Domains
How it works:
- Dedicated Linux renew and push certificates to RouterOS / Mikrotik
- After CertBot renew your certificates
- The script connects to RouterOS / Mikrotik using DSA Key (without password or user input)
- Delete previous certificate files
- Delete the previous certificate
- Upload two new files: Certificate and Key
- Import Certificate and Key
- Change SSTP Server Settings to use new certificate
- Delete certificate and key files form RouterOS / Mikrotik storage
Installation on Ubuntu 16.04
Similar way you can use on Debian/CentOS/AMI Linux/Arch/Others
Download the repo to your system God of war 3 pc cd-key.
Edit the settings file:
| Variable Name | Value | Description |
|---|---|---|
| ROUTEROS_USER | admin | user with admin rights to connect to RouterOS |
| ROUTEROS_HOST | 10.0.254.254 | RouterOSMikrotik IP |
| ROUTEROS_SSH_PORT | 22 | RouterOSMikrotik PORT |
| ROUTEROS_PRIVATE_KEY | /opt/letsencrypt-routeros/id_dsa | Private Key to connecto to RouterOS |
| DOMAIN | mydomain.com | Use main domain for wildcard certificate or subdomain for subdomain certificate |
Change permissions:
Generate DSA Key for RouterOS
Make sure to leave the passphrase blank (-N ')
Send Generated DSA Key to RouterOS / Mikrotik
Setup RouterOS / Mikrotik side
Check that user is the same as in the settings file letsencrypt-routeros.settings
Check Mikrotik ssh port in /ip services ssh
Check Mikrotik firewall to accept on SSH port
CertBot Let's Encrypt
Install CertBot using official manuals https://certbot.eff.org/#ubuntuxenial-other
for Ubuntu 16.04
In the first time, you will need to create Certificates manually and put domain TXT record
follow CertBot instructions
Usage of the script
To use settings form the settings file:
To use script without settings file:
To use script with CertBot hooks for wildcard domain:
To use script with CertBot hooks for subdomain:
Edit Script
You can easily edit script to execute your commands on RouterOS / Mikrotik after certificates renewalAdd these strings in the «.sh» file before «exit 0» to have www-ssl and api-ssl works with Let's Encrypt SSL
Licence MIT
Copyright 2018 Konstantin Gimpel
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the 'Software'), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED 'AS IS', WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
This repo contains information on setting up a FreeACS server with ibvirt and a Mikrotik x86 demo system,.
Background
This guide and repo allows research into TR-069 as covered by @info_dox at B-Slides Edinburgh. This repo is for others who wish to wargame out, or build upon his excellent work.
More information on that, and a video of his talk, can be found here
Prerequisites
To begin, you will need to collect some files:
- ubuntu-14.04.5-server-amd64.iso SHA256: DDE07D37647A1D2D9247E33F14E91ACB10445A97578384896B4E1D985F754CC1
- all_packages-x86-6.39.3.zip SHA256: 5BAC1EA32BFCA56822FA2C902C31B3E27349E4F22B6F9E3482BA870184DA6BA8
- mikrotik-6.39.3.iso SHA256: 22D6B47F15FA8B0E15728C49086390AF30FE1C476847F0F1878A8FB624DB022E
- FreeACS files - a copy is included in this repo
- Virtual platform of choice. Ill be using VMWare ESXi here
- A demo Mikrotik license key from here
A fair bit of this information was cleaned from the user TheKitchen on the mikrotik forums so thank you to him/her.
Infrastructure Setup
Ubutu FreeACS VM
Create a VM of reasonable size. I went with:
- 1GB RAM
- 10GB SCSI HDD
- 1 x VMXNET3 NIC
- hostname
free-acs.example.comon192.168.10.9provisioned with a fixed lease in DHCP.
Do a basic Ubuntu install, my preference is to use LVM, as this makes splitting out /var /tmp /home, etc. much easier.
Package Selections
When prompted which package selections to install, select:
User Setup
I created a user called busby / phormulateaplan and let the installation complete.
Post Install Setup
I always like to have an environment with the corect tools so now run
I have installed three text-mode browsers as this allows testing while setting up.
Installing FreeACS
Having now set up our environment, I suggesting cloning this repo to your VM.
Now, let us install the FreeACS software:
The script will prompt for a root MySQL password. I went for redframewhitelight. The script will additionaly ask for a password for the FreeACS database user. For this, I went with twilightzone as that's where we're heading.
After some time, the script will complete and we can proceed to the post-install fixes.
Post Install fixes
As outlined in the talk, one could easily make these edits via a sed or two. I'll do this manually for posterity.
First, edit /var/lib/tomcat7/conf/catalina.properties and find the string common.loader then append ,${catalina.base}/common,${catalina.base}/common/*.properties save the file and exit
Second, edit /etc/init.d/tomcat7 appending the line so it reads # Required-Start: $local_fs $remote_fs $network $mysql then save the file and exit.

Third, edit /var/lib/tomcat7/common/xaps-stun.properties and set the primary.ip value so it reads primary.ip = 0.0.0.0 save and exit the file.
NB: If you are not running this on a test LAN behind a firewall, you would change that to something else. Perhaps 192.168.88.1 if you intend only using the libvirt interface to administer CPE.
Lastly, restart tomcat for the changes to take effect: sudo service tomcat7 restart
The default login will now be availble at http://freeacs.example.com where the login admin / xaps can be used.
Pre Mikrotik Prep Work
For this part, we need a device which will run a TR-069 client. If you have routers to hand, connect them up. I am going to walk through the process of building a Mikrotik x86 router using KVM/libvirt.
Before we begin, ssh to Ubuntu host, and accept the SSH key. This allows the use of virt-manager remotely.
At this point, sign up for a free Mikrotik account.
Mikrotik Router VM x86
Using virt-manager, create a VM with the following specs:
- 128MB RAM
- 50M HDD
- NIC#1
RTL8139connected tomacvtap0which gives this node a192.168.10.10/24IP from you DHCP server - NIC#2
e1000connected tovnet0switch192.168.88.254/24the green (LAN) interface of the rotuer node - CD-ROM connected to
mikrotik-6.39.3.iso - Boot Order
CD-ROM -> HDD - VM set to start on boot
NB: A good way to remember which NIC is which, is to remember the three R's: Realtek NIC / Red Interface / Routable to the internet
Setting up Mikrotek
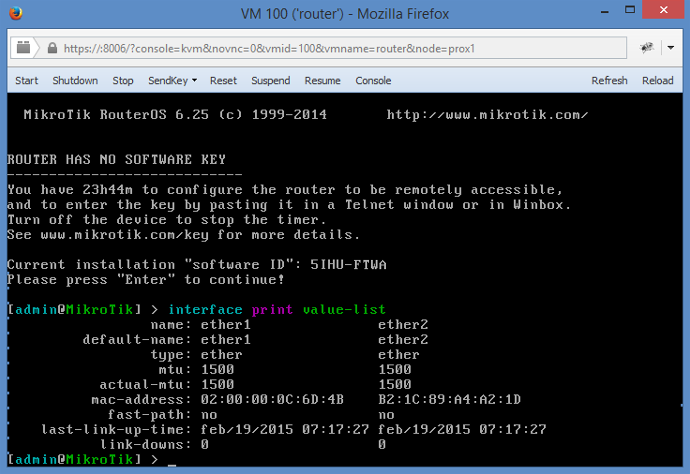
On first boot, the VM will show a console. Log in with admin / <blank password> and copy the software ID:
On the Mikrotik page, request a demo key, and be sure to copy and paste the software ID exactly as shown.
A key will be generated, which can be installed with winbox.exe or via telnet. I'll use telnet.
Initial Setup
Our next step is to configure the router for inital setup. Laziness being the mother of invention, I simply typed system reset-configuration which will bring the router up with a factory configuration, including DHCP on the red interface.
iAfter reboot, we can check the IP of the device:
applying License
Now that the VM has an IP, telnet to it and paste the license into the console:
NB: The key above is not a valid software license, it's the output of uuidgen piped into base64
After another reboot, confirm that the key is installed correctly:
Notice the subtle chnage in the output regarding the key and support. Now we can install the TR-069 client. Which is, after all, the point of going to all this trouble.
TR-069 Client Install
Before we install the TR-069 package, run a free resources check:
We can see 21MB of space, which is more than enough for a 900KB TR-069 agent. This is uploaded via FTP:
Upload TR-069 package
Once the package is uploaded, go back to the telnet session and confirm the file is there:
On reboot:
Enable TR-069 on client router
The following Script will allow the Mikrotek to check in with the server freeacs.example.com
Set TR069 Username to Ether1 mac address
When the Mikrotek comes back up, it will then start checking in with freeacs.example.com
Managing Routers
Login to FreeACS, click support > search amd click the search button.
The Mikrotek will show up with the MAC Address as the unit ID. The device can be managed via TR-069.
Create profiles by clicking Easy provisioning > profile for customer configs using TR-069 parameters. Profiles can be pushed to the CPE by clicking Support > search > Unit Configuration
Running Router OS Scripts
Via the RouterOS CLI
This can be done by creating the desired configuration via the routerOS CLI, then exporting to a text file named, for example, ABCD-E12F.alter. Then upload the file via Files & Scripts in FreeACS, upload and save the file using the TR-069_Script as the file type.
From Advanced Provisioning
Go to advanced provisioning > Job > Create New Job
Type: TR069 ScriptGroup: All profiles (or create a customer group via advanced provisioning group)Script: (the script you just uploaded)
Via Direct Push
Click Advanced provisioning > Job > Job overview, select the newly created job and click start, this will now push the RouterOS CLI to your Mikrotek
Wrap-up
A final suggestion from me, as with all thse sortso f security VMs, be they form @vulnhub or @HTB or wherever, set the disk to non-persistent so yo can knock them down over and over again..
On that note, my thanks to Darren Martyn for an interesting talk, as well as Mikrotik for giving dmeo licenses at no cost, and all the community out there hacking, breaking and security things.